This is the FPGA board on which the cryptoprocessor is embedded.
It is used for cryptographic simulations with changing security parameters flexibly.
The parameter settings are able to be controlled from the USB-connected PC.
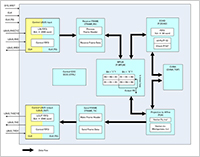
Enlarge Image Figure 2: Calculation architecture
In the Kintex-7 on the board shown in Fig.1, the cryptoprocessor is embedded.
This figure shows the details of the calculation architecture.
It consists of several parts such as elliptic curve cryptography, Montgomery powering ladder,
vector multiplication (CVMA : cyclic vector multiplication algorithm), and pairing.
It flexibly accepts many kinds of parameter settings.
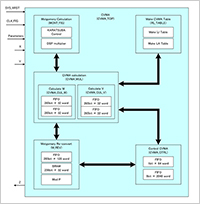
Enlarge Image Figure 3: Cyclic vector multiplication algorithm (CVMA)
This figure shows the architecture of cyclic vector multiplication algorithm. It uses Montgomery representation for efficient multi-precision arithmetic. The cryptoprocessor supports many kinds of parameter settings for which CVMA plays an important role. That is, since CVMA is able to accept many parameter settings, then accordingly elliptic curve and pairing cryptographies on CVMA is also able to support a wide range of security parameters.
Enlarge Image
World’s first flexible security Secure Cryptoprocessor with adjustable security level
Information security technology is necessary for the Cloud and IoT era. Particularly, public key cryptography such as RSA cryptography and elliptic curve cryptography plays an important role since it enables digital authentications for users and devices. In addition, recent innovative secure applications such as ID-based cryptography and time release encryption need much more complicated cryptographies such as pairing-based cryptography. ID-based cryptography enables the use some ID of the user as the public key.
On the other hand, the performance of computers improves dramatically year by year, and their level of security to prevent eavesdroppers should become higher accordingly. However, it is not easy to seamlessly adjust the security level of devices because public key cryptographies are basically based on some difficult and complicated mathematic problems. As an example, the secure key length of RSA cryptography increases 512, 1024, 2048, and then 3072 bits. Accordingly, cryptoprocessors need to be upgraded together with their arithmetic architectures.
Now, Yasuyuki Nogami and colleagues at Okayama University and Tokyo Electron Device Ltd, supported by Japan Science and Technology Agency (JST) have developed a secure cryptoprocessor that is able to flexibly adjust the level of security without upgrading the device itself. The Okayama University secure cryptoprocessor device supports several kinds of recent cryptographies such as elliptic curve and paring-based cryptography.
The secure cryptoprocessor devices can respond to the requirements of a wide range of security strengths in between 256 to 5120 bits with elliptic curve and pairing-based cryptography. In addition, the secure cryptoprocessor device has a small circuit area size and practical calculation efficiency.
This is the world’s first Secure Cryptoprocessor that can change the scale of security levels flexibly without requiring changes in the hardware. This scalability is supported by the original idea of the Okayama group called cyclic vector multiplication algorithm (CVMA). It is mainly used for vector multiplication but it enables wide scalability for security parameters.
It is expected to be mounted into a wide range of ubiquitous terminals and IoT devices because the circuit scale is extremely compact with efficient calculation power.
-
Reference:
- Authors: Yasuyuki Nogami, Hiroto Kagotani, and Kengo Iokibe, Okayama University, Hiroyuki Miyatake and Takashi Narita, Tokyo Electron Device LTD.
- Title of original paper: FPGA Implementation of Various Elliptic Curve Pairings over Odd Characteristic Field with Non Super Singular Curves.
- Journal, volume, pages and year: IEICE Trans. E99-D, No. 4, 805-815, (2016).
- Digital Object Identifier (DOI): 10.1587/transinf.2015ICP0018
- Journal website: http://search.ieice.org/bin/summary.php?id=e99-d_4_805
- Affiliations: Graduate School of Natural Science and Technology, Okayama University.
- Department website: http://www.gnst.okayama-u.ac.jp/index_e.html