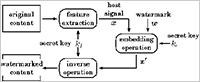
There are two main operations: one is feature extraction and the other is the embedding operation. Even if a secret key is used for feature extraction, a coalition of users will easily determine the selected host signal. The security problem in the feature extraction is solved in the proposed method by introducing a simple obfuscation method.
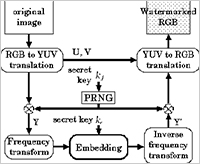
Enlarge Image Figure 2: Flowchart of the proposed method.
Before selecting the feature points of an original image, a pseudo-random number is multiplied to the luminance components to obfuscate the elements selected for embedding fingerprint signals.
Enlarge Image
Traceability for Multimedia Content: Protection against Pirated Copies
Digital Fingerprinting is a technique to identify users of illegal copies of multimedia content. It secretly inserts each user’s identity information into the content before sale. If an illegal copy is discovered, the illegal user(s) can be identified by the appropriate extraction of embedded information from the copy.
If a coalition of users compares their uniquely fingerprinted copies, they will find the differences, and hence they will be able to delete/modify the embedded information. In conventional systems, their algorithms for inserting/detecting the identities should be secret so that they cannot directly modify the information. However, if the system is standardized, the specifications of the algorithms must be disclosed in public except for a secret key.
Now, Minoru Kuribayashi at Okayama University has developed a simple method to enhance the security of conventional schemes.
For a coalition of users, several pirated copies are produced using standard images based on the consideration of possible attack scenarios, and the traceability from the pirated copies is evaluated through computer simulations.
The proposed scheme ensures the secrecy of the inserted fingerprint signal even if all algorithms except for the secret key are disclosed. Without the secret key, it is difficult for a coalition of users to effectively delete/reduce the inserted signals as fingerprints. What they can do is to globally degrade the given fingerprinted copies to produce a pirated version.
It is expected that the proposed method can be applied for the prevention of illegal distribution of multimedia content, which stimulates the industry of content distribution services via Internet.
-
Reference:
- Authors: Minoru Kuribayashi.
- Title of original paper: Simple countermeasure to non-linear collusion attacks targeted for spread-spectrum fingerprinting scheme.
- Journal, volume, pages and year: IEICE Trans. E99-D, No.1, 50-59, (2016).
- Digital Object Identifier (DOI): 10.1587/transinf.2015MUP0005
- Journal website: http://search.ieice.org/bin/summary.php?id=e99-d_1_50
- Affiliations: Graduate School of Natural Science and Technology, Okayama University.
- Department website: http://www.eng.okayama-u.ac.jp/eng_elec/html/
(Figure is in the next page)